Browse Resources
Information and Security Technologies -- Information and communications technologies
Resources |
|---|
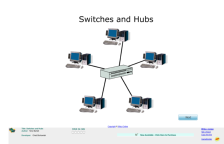
We all know how important computers are in our every day communication, but do you know how the computer in your office transfers information between the others? This online slideshow provided by Wisc-Online and the National Science Foundation explains the difference between a switch and a hub and...
This online, interactive lesson provided by Wisc-Online and the National Science Foundation explains how data is transferred through electrical conductors and the various configurations in which one can find these conductors. This slideshow goes into detail about the reasoning behind twisting cables...
This video, from the National Convergence Technology Center, is a part of the BILT Spotlight series that showcases essential elements of the BILT (Business and Industry Leadership Team) Model, which helps educators energize their relationship with employers and better align curriculum with workforce...
This article is the third in a series of nine that covers basic programming for designing and implementing embedded processors. The series concentrates on "high-level programming languages, specifically the C language." This article discusses how a high-level language program is translated into...
This article is the fourth in a series of nine that covers basic programming for designing and implementing embedded processors. The series concentrates on "high-level programming languages, specifically the C language." This article discusses generating code for procedures.
This article is the fifth in a series of nine that covers basic programming for designing and implementing embedded processors. The series concentrates on "high-level programming languages, specifically the C language." This article discusses register allocation and schedule, two important aspects...
This article is the sixth in a series of nine that covers basic programming for designing and implementing embedded processors. The series concentrates on "high-level programming languages, specifically the C language." This article discusses "how to analyze programs to estimate their run times. We...
This article is the eighth in a series of nine that covers basic programming for designing and implementing embedded processors. The series concentrates on "high-level programming languages, specifically the C language." This article discusses optimizing a program's energy consumption.
The ATETV project delivers web-based videos to connect students to careers in advanced technology. In this episode of ATETV, we learn about the work that computer forensic examiners do. Companies hire these experts to help recover and protect their data. Seeing the practical applications of what...
This 168-page report, developed after a 2022 cybersecurity education summit and published by the National Cybersecurity Training and Education Center (NCyTE), "examines new, emerging workforce requirements and develops a renewed national strategy for community colleges to continue contributing to...
|
| ← PreviousNext → |